COMPREHENSIVE SECURITY PLATFORM FOR PHYSICAL, VIRTUAL, AND CLOUD SERVERS
Virtualization and cloud computing have transformed the data center. Yet many organizations continue to use legacy security as they move from traditional physical environments to the modern data center where virtualization and cloud are the norm. Legacy security can increase operational complexity in virtual environments while decreasing host performance and virtual machine (VM) density. It leaves gaps in protection that can undermine the confidence to move mission-critical workloads to agile, low-cost cloud environments. Ultimately, using legacy security in the modern data center hinders the return on investment (ROI) of virtualization and cloud computing.
Protection from data breaches and business disruption
Trend Micro™ Deep Security™—available as software or as-a-service—is designed to protect your data center and cloud workloads from data breaches and business disruptions. Deep Security helps you achieve compliance by closing gaps in protection efficiently and economically across virtual and cloud environments.
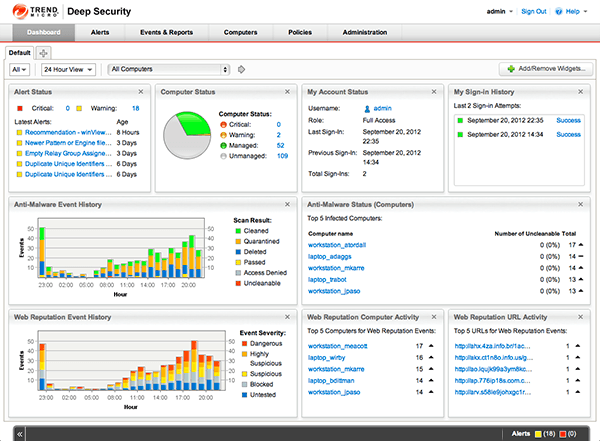
Multi-function security managed from a single dashboard
Deep Security features integrated modules including anti-malware, web reputation, firewall, intrusion prevention, integrity monitoring, and log inspection to ensure server, application, and data security across physical, virtual, and cloud environments. Deep Security can be deployed as a single, multifunction agent across all environments and simplifies security operations with a single management dashboard for all capabilities.
Seamless integration extends policies across cloud environments
Deep security seamlessly integrates with cloud platforms including Amazon web services (Aws), Microsoft Azure, and vMware vcloud Air enabling you to extend data center security policies to cloud-based workloads. with a wide range of capabilities optimized across environments, Deep security empowers enterprises and service providers to offer a differentiated and secure multi-tenant cloud environment to their users.

KEY BUSINESS ISSUES
![]()
Virtual Desktop security
preserve performance and consolidation ratios with comprehensive agentless security built specifically to maximize protection for vdi environments
![]()
Virtual Desktop security
preserve performance and consolidation ratios with comprehensive agentless security built specifically to maximize protection for vdi environments
![]()
Compliance
Demonstrate compliance with a number of regulatory requirements including pci Dss 3.0, hipaa, hitech, fisma/nisT, NERc, ssae 16, and more
ACCELERATE THE ROI OF CLOUD AND VIRTUALIZATION WITH SECURITY FOR THE MODERN DATA CENTER
Virtualization security
Deep Security protects virtual desktops and servers against zero-day malware and network-based attacks while minimizing operational impact from resource inefficiencies and emergency patching.
Cloud security
Deep Security enables service providers and modern data centers to offer a secure multi-tenant cloud environment with security policies that can be extended to cloud workloads and managed centrally with consistent, context-aware policies.
Integrated server security
Deep Security consolidates all server security functions into one comprehensive, integrated, and flexible platform that optimizes protection across physical, virtual, and cloud servers.
KEY ADVANTAGES
Accelerate Virtualization and Cloud ROI
- Yields more efficient resource utilization and management withhigher vm densities than traditional anti-malware solutions thatare not agentless
- Adds flexibility and defense-in-depth capabilities as a single,easy-to-manage multi-function security agent
- Delivers unparalleled performance via hypervisor-levelscanning deduplication
- Integrates with cloud platforms including Aws, Microsott Azure,and vMware vcloud Air, enabling organizations to manage theirphysical, virtual, and cloud servers with consistent andcontext-aware security policies
- Enables service providers to offer customers a secure publiccloud, isolated from other tenants via multi-tenant architecture
- provides auto-scaling, utility computing, and self-service to supportagile organizations running a software-defined data center
- Leverages Deep security’s tight integration with vMware toautomatically detect new vMs and apply context-based policiesfor consistent security across the data center and cloud
- integrates with vMware nsX™ Deep security extends the benefitsof micro-segmentation in the software-defined data center withsecurity policies and capabilities that automatically follow vMsno matter where they go
Prevent Data Breaches and Business Disruptions
- Detects and removes malware from virtual servers in real time with minimal performance impact
- Blocks malware that attempts to evade detection by uninstalling or otherwise disrupting the security program
- Shields known and unknown vulnerabilities in web and enterprise applications and operating systems
- Sends alerts and triggers proactive, prevention upon detection of suspicious or malicious activity
- Tracks website credibility and protects users from infected sites with web reputation threat intelligence from Trend Micro’s global domain-reputation database
- Identífies and blocks botnet and targeted attack command and control (c&c) communications using unified threat intelligence from Trend Micro’s global domain-reputation database
Achieve Cost-effective Compliance
- Addresses major compliance requirements for PCI DSS 3.0, as well as HIPAA, HITECH, NIST, and SAS 70 with one integrated and cost-effective solution
- Provides audit reports that document attacks prevented and compliance policy status
- Reduces the preparation time and effort required to support audits
- Supports internal compliance initiatives to increase visibility of internal network activity
- Leverages proven technology certified to Common Criteria EAL 4+
Maximize Operational Cost Reductions
- Eliminates the cost of deploying multiple software clients with a centrally managed, multi-purpose software agent or virtual appliance
- Reduces complexity with tight integrations with management consoles from Trend Micro, VMware, and enterprise directories
- Provides vulnerability shielding to allow secure coding and cost-effective implementation of unscheduled patches
- Reduces management costs by automating repetitive and resource-intensive security tasks, reducing false-positive security alerts, and enabling workflow of security incident response
- Significantly reduces the complexity of managing file-integrity monitoring with cloud-based event whitelisting and trusted events
- Detects vulnerabilities and software via Recommendation Scanning to detect changes and provide protection from vulnerabilities
- Ensures improved operational efficiency with a lighter, more dynamic smart agent that eases deployment to maximize resource allocation across the data center and cloud
- Matches security to your policy needs so fewer resources need to be dedicated to specific security controls
- Simplifies administration with centralized management across Trend Micro security products. Centralized reporting of multiple security controls reduces the challenge of creating reports for individual products


DEEP SECURITY PLATFORM MODULES
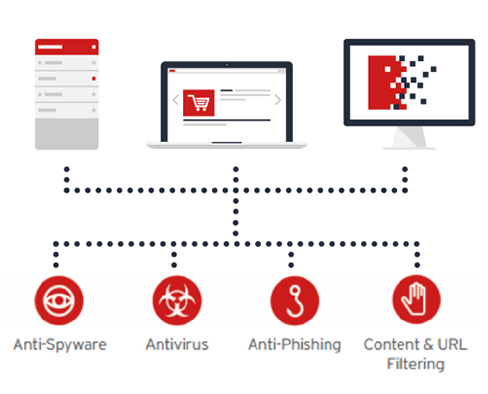
Anti-malware with Web Reputation
- Integrates VMware vShield Endpoint APIs to protect VMware Virtual machines against viruses, spyware, Trojans, and other malware with zero in-guest footprint
- Delivers an anti-malware agent to extend protection to physical, virtual, and cloud servers, including Aws, Mícrosoft, and vMware environments
- includes improved performance through vMware ESX-level caching and deduplication
- Optimizes security operations to avoid antivirus storms commonly seen in full system scans and pattern updates from traditional security capabilities
- protects from sophisticated attacks in virtual environments by isolating malware from critical operating system and security components
- integrates with the Trend Micro” smart protection Network” global threat intelligence for web reputation capabilities that strengthen protection for servers and virtual desktops
Intrusion Prevention
- Examines all incoming and outgoing traffic for protocol deviations, policy violations, or content that signals an attack
- Automatically protects against known but unpatched vulnerabilities by virtually patching (shielding) them from an unlimited number of exploits, pushing protection to thousands of servers in minutes without a system reboot
- Assists with compliance (PCI DSS section 6.6) to protect web applications and the data they process
- Defends against SQL injection, cross-site scripting, and other web application vulnerabilities
- Includes out-of-the-box vulnerability protection for all major operating systems and over 100 applications, including database, web, email, and FTP servers
- Provides increased visibility and control over applications accessing the network
Bidirectional Host-based Firewall
- Decreases the attack surface of physical, cloud, and virtual servers with fine-grained filtering, policies per network, and location awareness for all IP-based protocols and frame types
- Centrally manages server firewall policy, including templates for common server types
- Prevents denial-of-service attacks and detects reconnaissance scans
- Provides logging of firewall events at the host, enabling compliance and audit reporting that is especially critical for public cloud deployments
Integrity Monitoring
- Monitors critical operating system and application files, such as directories, registry keys, and values, to detect and report malicious and unexpected changes in real time
- Uses Intel TPM/TXT technology to perform hypervisor integrity monitoring for any unauthorized changes to the hypervisor, thereby extending security and compliance to the hypervisor layer
- Reduces administrative overhead with trusted event tagging that automatically replicates actions for similar events across the entire data center
- Simplifies administration by greatly reducing the number of known good events through automatic cloud-based whitelisting from Trend Micro” Certified Safe Software Service
Log Inspection
- Collects and analyzes operating system and application logs in over 100 log file formats, identifying suspicious behavior, security events, and administrative events across your data center
- Assists with compliance (PCI DSS section 10.6) to optimize the identification of important security events buried in multiple log entries
- Forwards events to SIEM system or centralized logging server for correlation, reporting, and archiving
PLATFORM ARCHiTECTURE
- Deep Security Virtual Appliance. Transparently enforces security policies on VMware vSphere Virtual machines for agentless anti-malware, web reputation, intrusion prevention, integrity monitoring, and firewall protection—coordinating with Deep security Agent, if desired, for log inspection and defense in depth.
- Deep Security Agent. Enforces the data center’s security policy (anti-malware, intrusion prevention, firewall, integrity monitoring, and log inspection) via small software component deployed on the server or virtual machine being protected (can be automatically deployed with leading operational management tools like chef, puppet, and Aws Opsworks).
- Deep Security Manager. powerful, centralized management console: role-based administration and multi-level policy inheritance allows for granular control. Task-automating features such as recommendation scan and Event Tagging simplify ongoing security administration. Multi-tenant architecture enables isolation of individual tenant policies and delegation of security management to tenant admins.
- Global Threat Intelligence. Deep Security integrates with Trencl Micro Smart Protection Network to deliver real-time protection from emerging threats by continuously evaluating and correlating global threat and reputation intelligence for websites, email sources, and files.
PLATFORM ARCHITECTURE
Microsoft® Windows®
- Windows XP, Vista, 7, 8, 8.1 (32-bit/64-bit)
- Windows Server 2003 (32-bit/64-bit)
- Windows Server 2008, 2008 R2, 2012, 2012 R2
- XP Embedded
Linux1
- Red Hat® Enterprise 5, 6 (32-bit/64-bit)2
- SUSE® Enterprise 10, 11 (32-bit/64-bit)2
- CentOS 5, 6 (32-bit/64-bit)3
- Ubuntu 10, 12, 14 (64-bit)3
- Oracle Linux 5, 6 (32-bit/64-bit, LTS only)3
- CloudLinux 5, 6 (32-bit/64-bit)3
- Amazon Linux4
Oracle Solaris™ 5, 6
- OS: 9, 10, 11 (64-bit SPARC), 10, 11 (64-bit x86)7
- Oracle Exadata Database Machine, Oracle Exalogic Elastic Cloud and SPARC Super Cluster via the supported Solaris operating systems
UNIX6
- AIX 5.3, 6.1, 7.1 on IBM Power Systems8
- HP-UX 11i v3 (11.31)9
VIRTUAL
- VMware® vSphere: 5.0/5.1/5.5, vCloud Networking and Security 5.1/5.5, View 4.5/5.0/5.1, ESX 5.5, NSX 6.1
- Citrix®: XenServer10
- Microsoft®: HyperV10
Key certifications and Alliances Amazon Advanced Technology partner certified red hat ready cisco ucs validated common criteria EAL 4+
- EMc vspEX validated
- Hp Business partnership
- Microsoft Application protection program
- microsoft certified partnership
- NetApp flexpod validated
- Oracle partnership
- pci suitability Testing for HIps (Nss labs) VCE Vblock valiclatecl Virtualization by VMware


